Learn how Docguardian can help you maintain your system security plan (ssp).
Take the complexity out of documentation with RG360.
RG360 stands out as the ideal solution to assist customers in generating and maintaining their System Security Plan (SSP) for FedRAMP due to several key factors. RG360 is specifically designed to streamline and simplify the complex process of SSP creation and maintenance, ensuring that customers can efficiently navigate the stringent requirements of FedRAMP compliance.
![webdeveloper_3-[Converted]](https://fabriclake.com/wp-content/uploads/2023/11/webdeveloper_3-Converted.png)
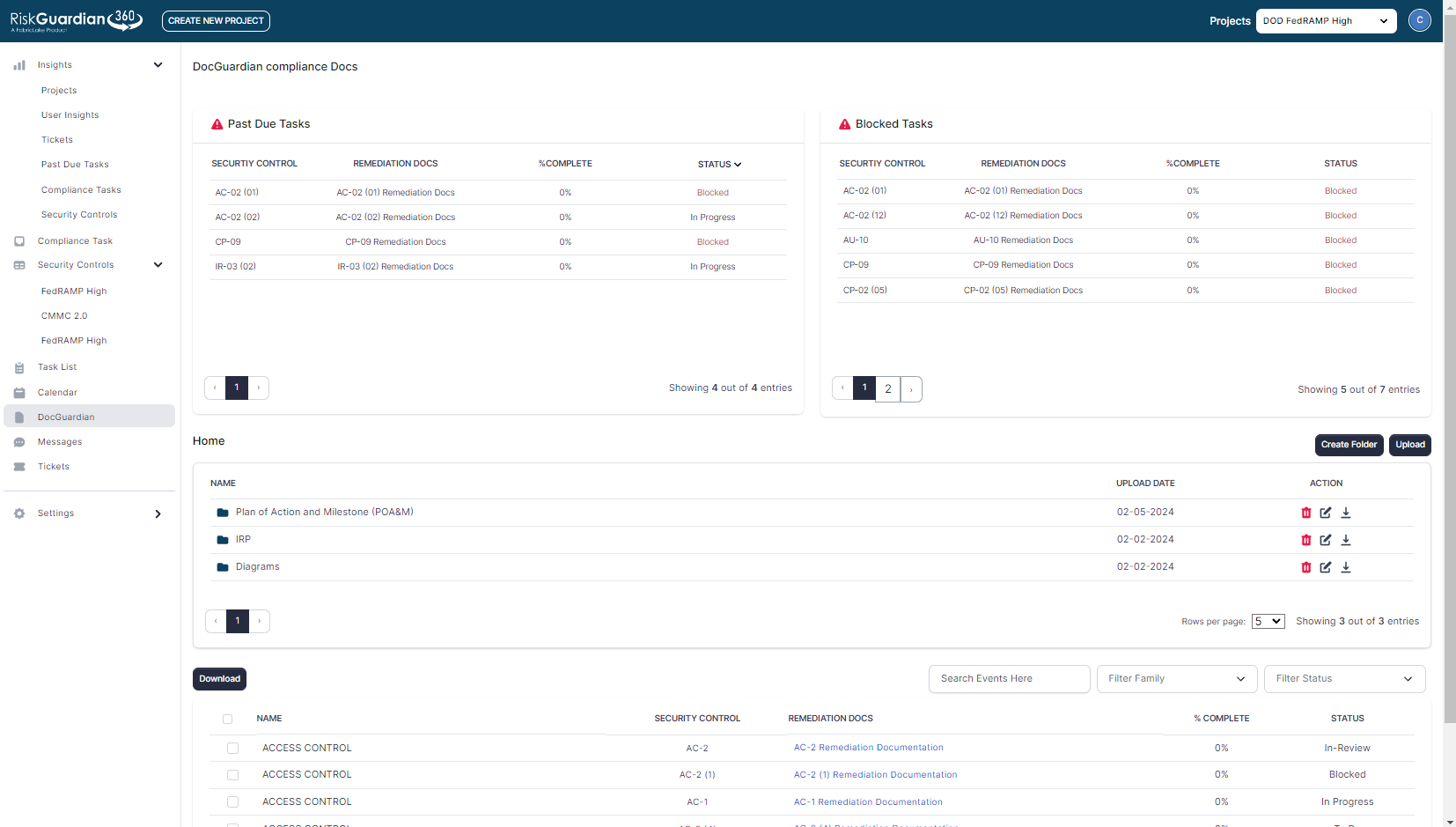
Simplifying the understanding and management of the SSP.
RG360 offers comprehensive features tailored to the specific needs of FedRAMP SSP generation and maintenance. These features include intuitive tools for gathering and organizing the extensive documentation required for SSPs, as well as built-in templates and guidelines that align with FedRAMP standards.
Stay up-to-date with NIST Framework
Overall, RG360’s robust capabilities, user-friendly interface, and dedication to staying current with FedRAMP standards make it the optimal choice for customers seeking an efficient and reliable tool to generate and maintain their SSP for FedRAMP compliance.
Managing Complex Federal Compliance Landscape with Smart, Efficient, and Secure AI.
AN AI Platform to assist with compliance
Simplify the intricate world of compliance using Artificial Intelligence.
We understand the complexity of FedRAMP, with its often unclear and ambiguous requirements that necessitate the expertise of a 3PAO to provide clarity and translate these demands into manageable remediation steps that can incur substantial costs running into hundreds of thousands.
Achieve deadlines more efficiently with RiskGuardian360’s AI capabilities.
Cost and Resource Savings
Streamlining compliance efforts with RiskGuardian360 AI can significantly reduce costs and resources required for trial and error assessments and remediation.
Reduced Human Errors
AI Automation minimizes human errors in compliance management, improving accuracy and reducing risk.
Comprehensive Reporting
RiskGuardian360 AI generates detailed compliance reports for easy auditing and demonstrating adherence to NIST standards.
Scalability
RiskGuardian360 AI can handle a high volume of security controls and compliance projects, making it suitable for organizations with complex systems and numerous compliance requirements.
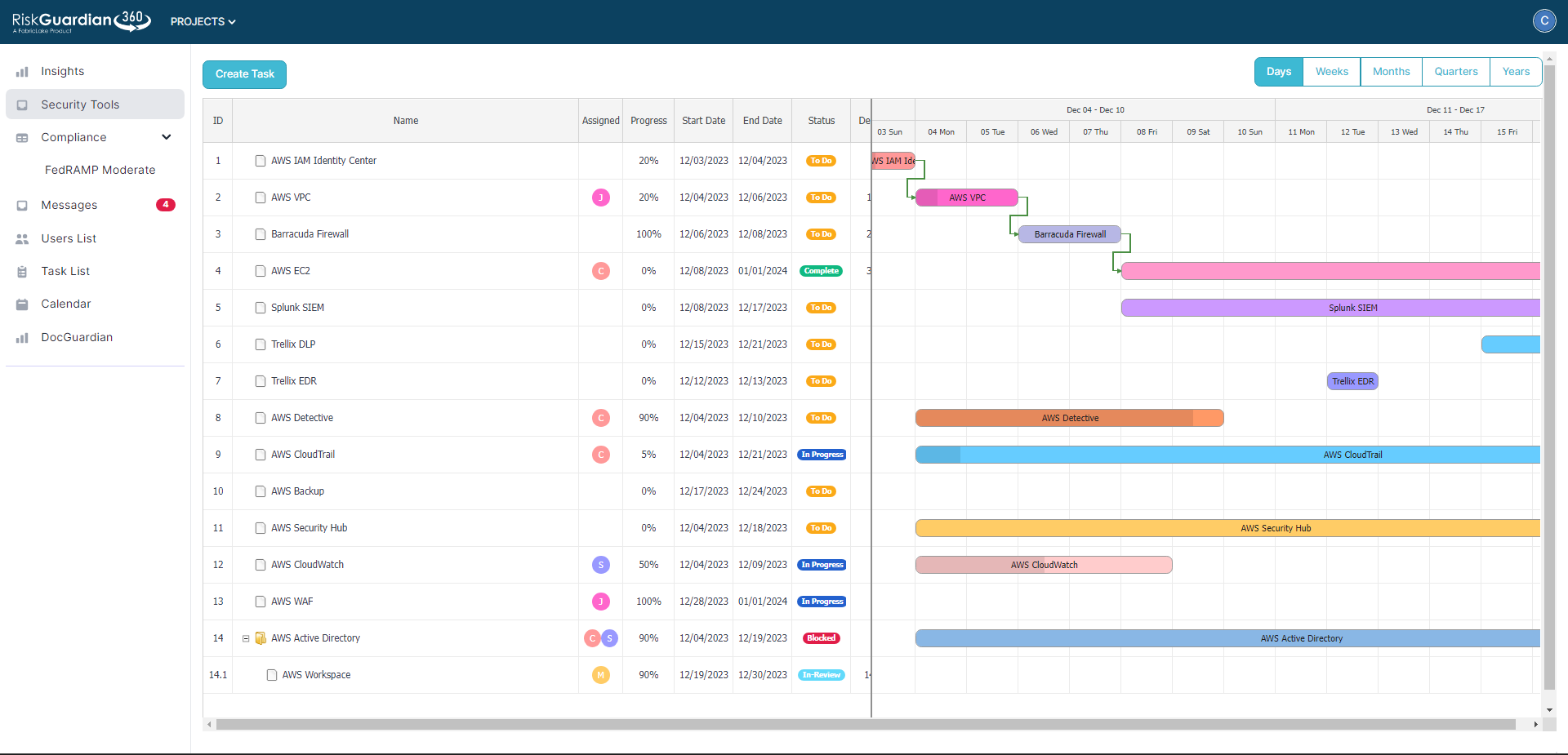
Streamline Tools Deployment
RiskGuardian360 AI offers detailed, user-friendly instructions for deploying and configuring security tools, ensuring adherence to compliance requirements.
Remediation Strategies
RiskGuardian360 generates tailored step-by-step remediation instructions for each security control, aligning with NIST standards and organizational needs.
Adaptive
RiskGuardian360 can adapt its recommendations based on the evolving threat landscape and changing compliance requirements.
Data-driven Support
RiskGuardian360 AI can provide data-driven insights and suggestions for optimizing security controls and tool configurations.
Simplify requirements
RiskGuardian360 processes ambiguous requirements and provides instructions that are easily understandable to humans.

Frequently Asked Questions
Auditors will have read and able to generate reports.
We have worked with numerous auditors and what we have recommended to them was to use our “Inspector”, our chatbot trained and contained within the system to be able to query and answer any question related to the project.
A real life use case:
User: Show me what has been completed in the “AC security controls”?
Inspector will crawl through the database, find all the answers and present the answers in an understandable format.
User: Does the AC security controls in this FedRAMP Moderate SSP lack any artifacts or evidence?
Within a minute, Inspector will come back with an intelligent response outlining what has been collected and the auditor can either determine if it requires more or not.
RiskGuardian360 is a System of Records and Intelligence that utilize NLP to properly answer questions.
Project Owners or Project Managers will automatically be assigned the administrator role.
PM’s will be able to:
- Create projects
- Create / delete users
- Reset passwords
- Create / modify / delete tasks
- Assign tasks
- Generate reports
- Landing Project Management page
- Audit Tasks
- Add / change / delete / rewrite tickets
- Get an overall view of tickets
CA-7 – Continuous Monitoring
CSOs authorized via the Agency path with more than one agency ATO are now obligated to conduct joint monthly Continuous Monitoring (ConMon) meetings involving all agencies.
SC-8, SC-8 (1), SC-13, and SC-28
Mandates the utilization of 140-2 FIPS-validated or NSA-approved cryptography for encrypting ALL data-at-rest and data-in-transit.
CM-6 – Configuration Settings
Requires adherence to DoD Security Technical Implementation Guides (STIGs), though it accepts CIS Level 2 benchmarks if a STIG is unavailable. This is a departure from Rev 4, which only mandated CIS Level 1 benchmarks.
NOTE: According to the Center for Internet Security, the Level 1 profile is considered a fundamental recommendation with manageable performance impact and swift implementation. Conversely, the Level 2 Profile is viewed as a “defense in depth” measure, ideal for security-critical environments, but potentially carrying significant organizational impact if not implemented carefully.
SC-7(b) – Boundary Protection
Demands subnet isolation for both public and private system components.
For further details, please refer to the FedRAMP subnets whitepaper.





