Federal Compliance Project management grc
Streamline Federal Compliance with a Unified Project Management & GRC Platform.
Streamlining federal compliance through a unified platform that integrates project management, ticketing, and GRC offers a wide array of benefits, including heightened operational efficiency, increased accountability, and seamless adherence to federal regulations.
![projectmanager_online_1-[Converted]](https://fabriclake.com/wp-content/uploads/2023/11/projectmanager_online_1-Converted.png)
The selected Security Compliance controls during Project creation are automatically updated with the most recent version of FedRAMP HIGH.
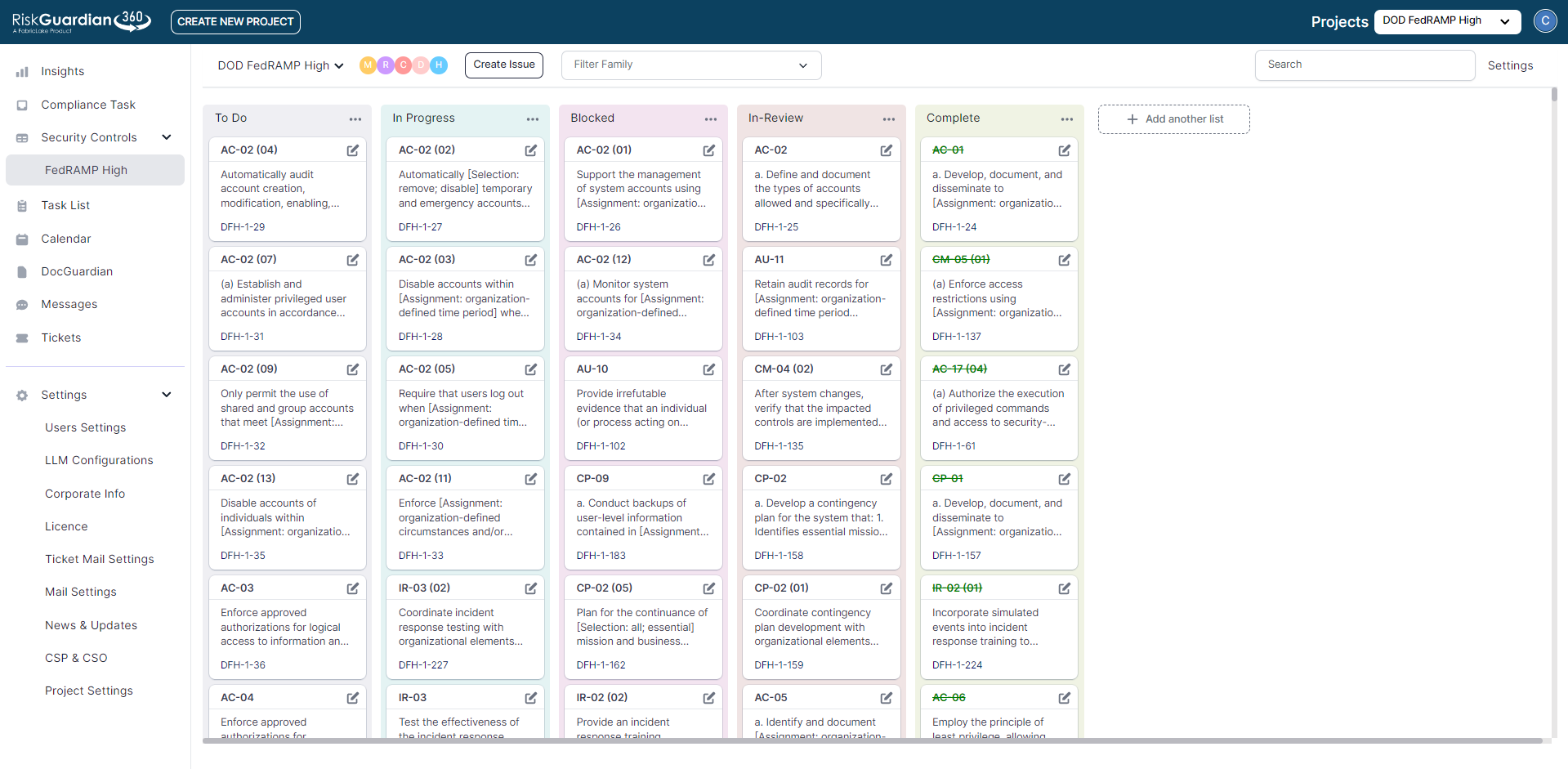
The Gantt is automatically populated with Security Tools from the Project Creation for the purpose of prioritization, assignments, and setting dates.

Managing Complex Federal Compliance Landscape with GRC Project Management Platform.
Unified Platform for compliance
Simplify the intricate world of compliance with RiskGuardian360’s project management functionalities.
We recognize the challenges of managing Federal compliance projects, characterized by often unclear and ambiguous requirements. RiskGuardian360 serves as a System of Intelligence that simplifies the federal compliance landscape.
Meet Organizational Benchmarks with Effective Project & Tasks Management
Task Centralization
Efficiently oversee tasks across all ongoing processes through a specialized view that organizes tasks based on their due dates.
Employee Accountability
Delegate tasks to specific agents to define ownership and monitor progress while maintaining a comprehensive record of updates through audit histories.
Assign Users and Groups
Automatically allocate tasks to individual users upon their creation or assign them to a group of users to evenly distribute workloads.
Task Centralization
Efficiently oversee tasks across all ongoing processes through a specialized view that organizes tasks based on their due dates.
Pre-set Tasks
Incorporate pre-set tasks into processes that receive automatic updates based on platform actions.
Automated Due Dates
Set the task’s due date based on the process creation date or other relevant events as needed.
Set Task Requirements
Assess whether a task is necessary for the comprehensive completion of the associated process.
Task Prioritization
Organize tasks in the preferred sequence for a standard task list within each process.
Customized Tasks
A specialized Tasks User Interface tailored for Security Controls, seamlessly integrated with Governance, Risk, and Compliance (GRC) elements, while harmonizing with standard project management methodologies.

Frequently Asked Questions
Auditors will have read and able to generate reports.
We have worked with numerous auditors and what we have recommended to them was to use our “Inspector”, our chatbot trained and contained within the system to be able to query and answer any question related to the project.
A real life use case:
User: Show me what has been completed in the “AC security controls”?
Inspector will crawl through the database, find all the answers and present the answers in an understandable format.
User: Does the AC security controls in this FedRAMP Moderate SSP lack any artifacts or evidence?
Within a minute, Inspector will come back with an intelligent response outlining what has been collected and the auditor can either determine if it requires more or not.
RiskGuardian360 is a System of Records and Intelligence that utilize NLP to properly answer questions.
Project Owners or Project Managers will automatically be assigned the administrator role.
PM’s will be able to:
- Create projects
- Create / delete users
- Reset passwords
- Create / modify / delete tasks
- Assign tasks
- Generate reports
- Landing Project Management page
- Audit Tasks
- Add / change / delete / rewrite tickets
- Get an overall view of tickets
CA-7 – Continuous Monitoring
CSOs authorized via the Agency path with more than one agency ATO are now obligated to conduct joint monthly Continuous Monitoring (ConMon) meetings involving all agencies.
SC-8, SC-8 (1), SC-13, and SC-28
Mandates the utilization of 140-2 FIPS-validated or NSA-approved cryptography for encrypting ALL data-at-rest and data-in-transit.
CM-6 – Configuration Settings
Requires adherence to DoD Security Technical Implementation Guides (STIGs), though it accepts CIS Level 2 benchmarks if a STIG is unavailable. This is a departure from Rev 4, which only mandated CIS Level 1 benchmarks.
NOTE: According to the Center for Internet Security, the Level 1 profile is considered a fundamental recommendation with manageable performance impact and swift implementation. Conversely, the Level 2 Profile is viewed as a “defense in depth” measure, ideal for security-critical environments, but potentially carrying significant organizational impact if not implemented carefully.
SC-7(b) – Boundary Protection
Demands subnet isolation for both public and private system components.
For further details, please refer to the FedRAMP subnets whitepaper.





